„If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.“
Bruce Schneier

„If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.“
Bruce Schneier
The vast majority of cybercrimes don’t have anything to do with a hacker’s skills or high-tech equipment. On the contrary, studies show that:
Average cyberattack damages resulting from insufficient training and employee negligence total $1,057,000 annually per company, with maximum damages topping out at over $200 million!
Almost all IT crimes are based on user misconceptions causing people to neglect information hygiene. These misconceptions can be divided into three groups:
The main job of information security specialists is to dispel these misconceptions and train corporate employees to adopt responsible IT habits and comply with information security rules.

— Bruce Schneier

My name is Timofey Skorenko. Over the past few years, I’ve been developing training courses on information security for Kaspersky Lab.
My portfolio includes:
and more.
Before transitioning to information security, I worked for many years as a science journalist in a number of publications, and also headed the editorial board of Popular Mechanics.
I also do personal trainings and lecture publicly on topics related to cybersecurity, science and technology.
You can download my detailed CV here.
— Richard A. Clarke
Information security awareness spans how to ensure the safety of information both digitally and on paper.
Most of the time, this doesn’t mean having the same specialized knowledge as information security officers, cryptographers and programmers, but rather good information hygiene (general rules for ordinary users to help them protect the data they work with).
Most data theft is based on social engineering, or the art of manipulating people so they give up confidential information. To steal a password from a corporate account, expensive information or just money, you don’t need special software or sophisticated technical training. It’s enough to know the basics of human psychology and how to adapt to the victim’s manner of communication.
Maintaining good information hygiene helps avoid losses from cybercrime, protects your company and its employees, and also ensures competitiveness in a modern market based almost entirely on digital technology.


Passwords are the first and main means of protecting information.
About 10% of all internet users’ passwords are a word or phrase from the top 25 most common passwords (123456, 123456789, qwerty, password, iloveyou, admin, etc.). These passwords are even used to protect corporate resources and accounts containing confidential information.
Information security training teaches users how to:
…and more.
Email is the new standard for modern communication. It’s used for personal and business correspondence, sending files and documents (including confidential), and registering on online resources.
Access to your email opens up unlimited doors for cybercriminals. They can hack almost any resource you’re registered in to gather what they need to rob you, blackmail you or steal corporate information.
But the most effective and dangerous cyberattack method, especially in the context of the massive migration to remote work due to COVID-19, is email phishing, a type of social engineering that helps scammers access your personal or work data via email.
Information security training teaches users:
…and more.

There’s nothing more relevant than the Internet in the 21st century. We use it to receive information, work, have fun, communicate, shop, exchange data, and more. In fact, it’s like a digital mirror of the real world, where surfing is the same as traveling.
But just like in the real world, the Internet is a dangerous place. Cybercriminals set all sorts of traps to collect data or make money off of inexperienced and inattentive users. And this doesn’t just mean scam websites (although they’re the main issue), as even well-protected state portals can be infected with malicious code.
Information security training teaches users how to:
…and more.
Social media contains concentrated doses of user information. Cybercriminals can glean from a social media account the full name of a person, their address and phone number, how much they earn and where they store their savings, when they go on vacation and who they travel with. People on social media carelessly post pictures of their passports and plane tickets, confidential documents and information about deals at work, where their apartment is located and how to get inside.
Today, almost everyone has accounts on several social networks, including Facebook and Vkontakte, Twitter and Instagram, TikTok and Youtube. And they’re filled with information about users’ lives, families and jobs.
Then there are messengers, both integrated in social media and independent (Telegram, WhatsApp, Viber, Skype). Cybercriminals exploit them to carry out phishing attacks. For example, in 2017, cybercriminals stole almost $500,000 by sending phishing messages to members of the Enigma blockchain project through Slack, a corporate messenger.
Information security training teaches users how to:
…and more.


If the internet is its own little world, then your computer is its front door. But it’s not just the front door! We also use computers for work and play, to create new things and to study the past. We rely on them to store gigabytes of valuable data, including work documents, archives, pictures, outlines, as well as passwords and other ways of accessing network resources.
Users are often irresponsible about their computer’s “health.” They don’t use antivirus software, disable security systems, and install unlicensed programs. This leads to some unfortunate consequences. For example, a 2017 study by Kaspersky Lab showed that 42% of personal computers in Russia are infected with malware!
Information security training teaches users:
…and more.
Mobile phones are more than just a way to communicate — they’re a universal tool for managing your life and work. We use them to talk and message, search for information online, pay for purchases, take photos and shoot videos. This means that mobile phones are a huge repository of information about their owners, and cybercriminals exploit this.
Cybercriminals don’t even need to steal phones. All they need to do to get full control is install a tracking program on them, for example, when a user connects to a public Wi-Fi network. Then, for example, scammers can read text messages with bank confirmation codes to bypass two-factor authentication and steal money from your accounts.
Information security training teaches users how to:
…and more.


Everyone, regardless of their age, social status and job, should know how to properly handle the confidential information they have access to.
It’s also crucial to understand that any information you handle at work might be confidential by default, otherwise known as the “presumption of confidentiality.” In other words, it must first be proven that information can be shared.
Not all information that isn’t subject to disclosure has a “classified” stamp or some other privacy marking. It’s most often the case that confidentiality is determined by indirect and non-universal signs. In fact, more than 60% of leaks in large tech companies occur because of negligent employees with access to confidential data!
Information security training teaches users how to:
…and more.
Personal data is any information directly or indirectly related to the data subject, including first and last name, date of birth, passport and driver’s license number, religion, income, place of work, etc. Once a scammer gets a certain amount of a victim’s personal data, they can use it for their own purposes (for example, to steal their identity and commit crimes without any of the blame).
But handling personal data properly is just as much a legal responsibility as it is an information security issue. Almost every country has personal data protection laws where violations can cost companies a fortune in fines.
For example, in 2018, a serious leak of customer personal data was discovered in British Airways databases. The leak fell under the jurisdiction of the GDPR (General Data Protection Regulation) in the European Union and European Economic Area, and the company was forced to pay €205 million in fines!
Also, the GDPR and other local regulations most often apply beyond the borders of certain countries to also apply to citizens living and working abroad. In other words, knowing how to properly handle personal data requires careful attention and can save a company from major problems.
Information security training teaches users how to:
…and more.

— Paul Herbka
Kaspersky Automated Security Awareness Platform (ASAP) is a training course currently spanning 12 topics (45-50 thousand words in each). Platform materials are based on a learning model including more than 700 practical skills for trainees. The platform allows you to gain knowledge and consolidate skills in the field of cybersecurity culture.
K-ASAP topics:
Kaspersky Adaptive Online Training (KAOT) program is a training course based on adaptive learning principles. Adaptive learning is an educational method that adapts the learning process to the capabilities, knowledge and confidence of users. KAOT constantly analyzes user knowledge of the subject and changes the learning trajectory depending on what information they currently need.
KAOT topics:
Stay Safe, Stay Secure is a course prepared in collaboration with Area9 Lyceum to help improve information security during the COVID-19 pandemic. The module includes 21 theory slides (each consisting of 2-6 pages), and 17 test questions.
Phishing attack simulator is the most effective tool to assess employees’ practical skills in countering phishing threats. Phishing simulators are part of a range of platforms designed to raise awareness in the field of information security, including similar functionality in the Kaspersky ASAP platform.
The main work involved in creating a phishing simulator is actually developing phishing emails.
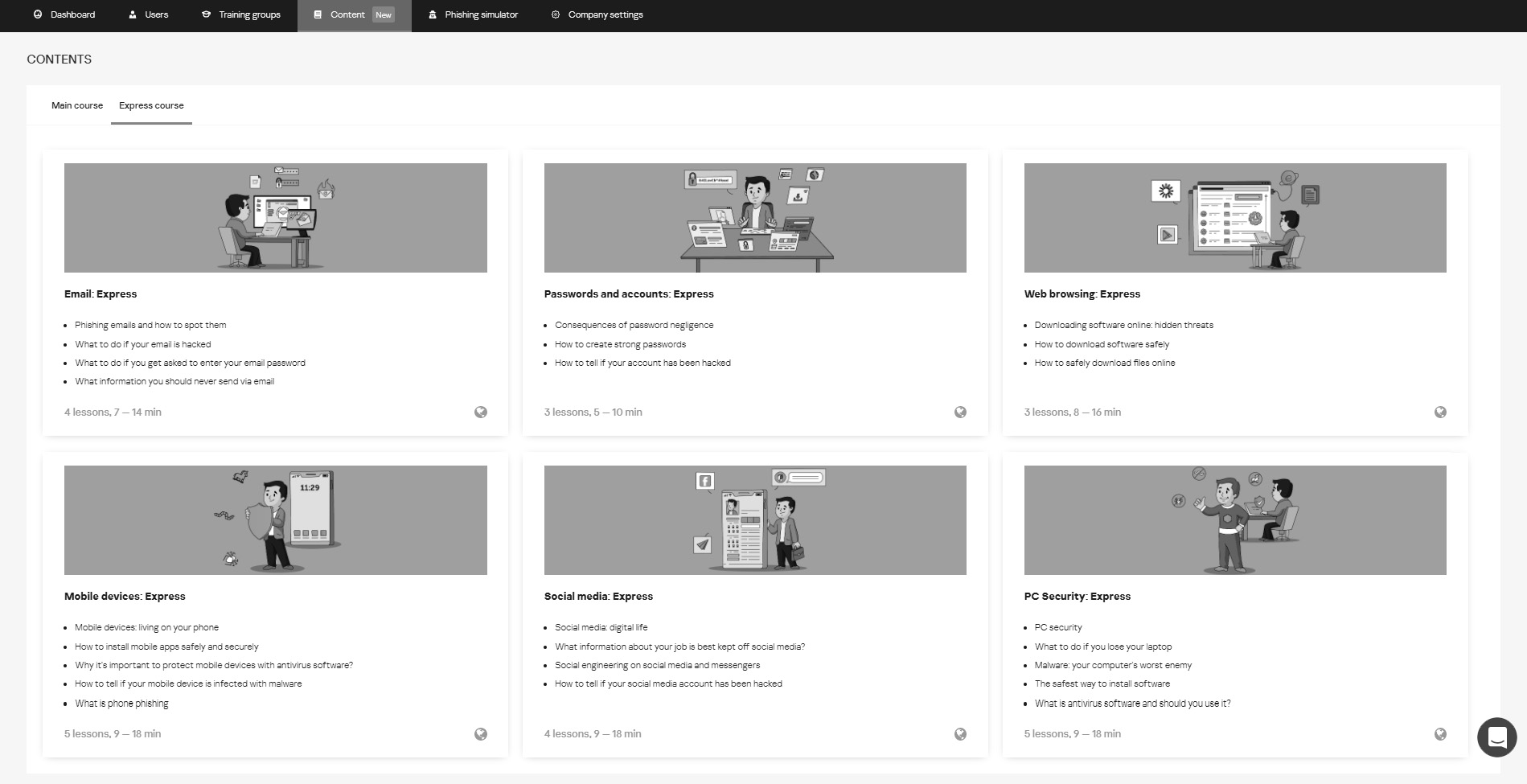
Kaspersky ASAP Express is a lightweight training course currently spanning 11 topics delivered in an interactive, playful format. The platform allows you to gain knowledge and consolidate skills in the field of cybersecurity culture.
K-ASAP Express topics:
The Privacy Awareness and Competence Testing program for information security was created using the Kaspersky Automated Security Awareness Platform (K-ASAP) for the TRAnsparency, Privacy and security for European citiZEns (TRAPEZE) initiative. TRAPEZE is an international educational project that received funding from the EU Horizon 2020 program, with the aim of enhancing the knowledge on information management. This project caters mainly to senior citizens residing within the EU, but individuals of at least 18 years old may participate regardless of age.

The Cyber Violence and Stalkerware Online Course is developed based on the Kaspersky Automated Security Awareness Platform (K-ASAP) as part of the DeStalk program. The DeStalk program is an international project aimed at reducing gender-based cyber violence, particularly against women. Obsessive behavior and the use of spyware are increasingly widespread; sexual harassment, bullying, cyberstalking, and other forms of cyber violence against women and girls not only go unpunished but often go undetected. The DeStalk project raises awareness about these forms of violence and calls on government authorities and public organizations to actively combat cybercriminals.

— Bruce Schneier
Creation of a competency model for company staff with different skill levels and a training plan based on the model. Management of the team creating the course content.
Public and corporate lectures on information security topics for various ages and social groups. Lecture cycles and stand-alone presentations on specific topics.
Development of a training strategy for corporate clients. Mixed training programs to increase staff awareness including courses, lectures, seminars and trainings.
Practical training on information security. Simulated attack practice and feedback on mistakes. Express trainings.
Gauging employee knowledge. Development of surveys, tests and simulated attacks.
Development of corporate information security policies in accordance with current legislation.
— James Snook
